In the ever-evolving landscape of healthcare, the need for robust security measures cannot be overstated. Healthcare organizations must navigate a labyrinth of regulations, one of the most pivotal being the Health Insurance Portability and Accountability Act (HIPAA). This legislation serves as both a shield and a sword for patients’ sensitive information. Among the myriad components that comprise HIPAA guidelines, administrative safeguards stand out as the cornerstone of an organization’s security strategy.
Understanding Administrative Safeguards
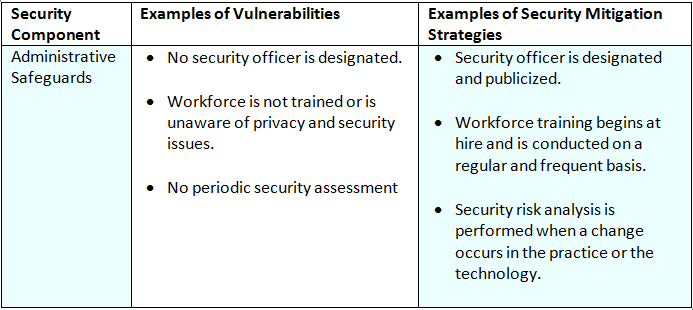
Administrative safeguards, much like the foundations of a grand edifice, provide stability and support to the entire spectrum of health information security. These safeguards encapsulate a range of policies and procedures that govern the management and protection of electronic protected health information (ePHI). They serve not only to fortify data integrity but also to instill a culture of security within the organization.
1. The Architect’s Blueprint: Policy Development
The first step in establishing comprehensive administrative safeguards is the formulation of rigorous policies. These policies should delineate the organizational protocols for accessing, using, and disclosing ePHI. Crafting these guidelines requires meticulous forethought—a blueprint that details how the organization plans to safeguard sensitive data, akin to an architect sketching the dimensions of a skyscraper before breaking ground.
Each policy must resonate with clarity, encompassing details such as user access controls, data handling procedures, and response strategies for security breaches. The mere existence of these policies lays the groundwork for a resilient security framework.
2. Personnel Training: Equipping the Guardians
Once the policies are established, the next step involves fostering a cadre of informed personnel. Training employees is akin to equipping guardians with the tools necessary to defend a castle. Each staff member should possess a deep understanding of their roles within the security landscape, comprehending how to navigate potential risks and vulnerabilities.
Regular training sessions, coupled with updated learning materials, ensure that knowledge remains current and employees are aware of emerging threats. This iterative process reinforces the organization’s commitment to safeguarding patient information and fosters a culture of security awareness.
3. Risk Assessment: The Sentinel’s Vigil
In the realm of data security, vigilance is paramount. Rigorous risk assessments function as a sentinel’s watch, identifying vulnerabilities and potential threats to ePHI. Organizations should conduct these assessments periodically, evaluating their internal environment and the external technological landscape.
Each identified risk necessitates a tailored mitigation plan, akin to a wise tactician devising specific strategies to counteract encroaching foes. Addressing these risks proactively not only fortifies data security but also preserves the trust embedded in the patient-provider relationship.
4. Incident Response Plan: The Emergency Protocol
No security shield is infallible; thus, a responsive framework is essential for times of crisis. An incident response plan is indispensable—a meticulously crafted guide that outlines the specific steps to be taken upon discovering a breach or suspected violation of ePHI security.
This plan should encompass clear roles and responsibilities, communication strategies, and post-incident reviews to identify areas for improvement. Like a fire drill practiced in schools, the execution of such a plan ensures that every member of the organization is prepared for action, minimizing chaos and confusion during an actual event.
5. Data Access Controls: The Portcullis
At the heart of administrative safeguards lies the concept of access control. Establishing stringent data access measures is paramount—functioning akin to a portcullis that protects the castle gates. These controls dictate who can access ePHI, under which circumstances, and through what means.
Implementing role-based access, where employees receive permissions based solely on their job function, reduces the risk of data exposure. Additionally, leveraging multi-factor authentication adds extra layers of security, reinforcing the barriers protecting sensitive information.
6. Regular Audits: The Guard’s Watchful Eye
To maintain an effective security posture, organizations must engage in habitual audits, much like a watchful eye scanning the horizon for any signs of danger. These audits assess compliance with established policies and analyze the efficacy of current security measures. They function as proactive checks that can uncover weaknesses before they are exploited.
Regular audits not only ensure adherence to HIPAA regulations but also take the organization a step further by fostering a culture of accountability and continuous improvement. Each audit serves as a learning opportunity, leading to adaptations that enhance the overall security framework.
7. Documentation and Reporting: The Chronicles of Security
Finally, the significance of thorough documentation and reporting cannot be overstated. This practice acts as the chronicler of security endeavors, detailing the steps taken to secure ePHI and the ongoing measures employed to uphold compliance. Detailed records facilitate understanding of past incidents, guide decision-making, and demonstrate an organization’s commitment to safeguarding patient information.
Proper documentation not only provides an operational roadmap but also serves as potential evidence in demonstrating compliance during regulatory audits.
Conclusion: The Symphony of Security
In conclusion, administrative safeguards are tantamount to the harmonious arrangement of instruments within a symphony. Each element plays a crucial role in creating a cohesive security strategy designed to protect sensitive health information. The successful implementation of these safeguards fosters both a secure environment and a lasting trust that patients place in their healthcare providers. By understanding and prioritizing these administrative measures, organizations will not only comply with HIPAA but will also become stalwarts in the realm of data security, championing the protection of patient privacy in an increasingly complex digital age.
